A smart contract vulnerability within the decentralized finance (DeFi) lending protocol Pike Finance has resulted in the theft of $1.6 million worth of cryptocurrency over a span of three days.
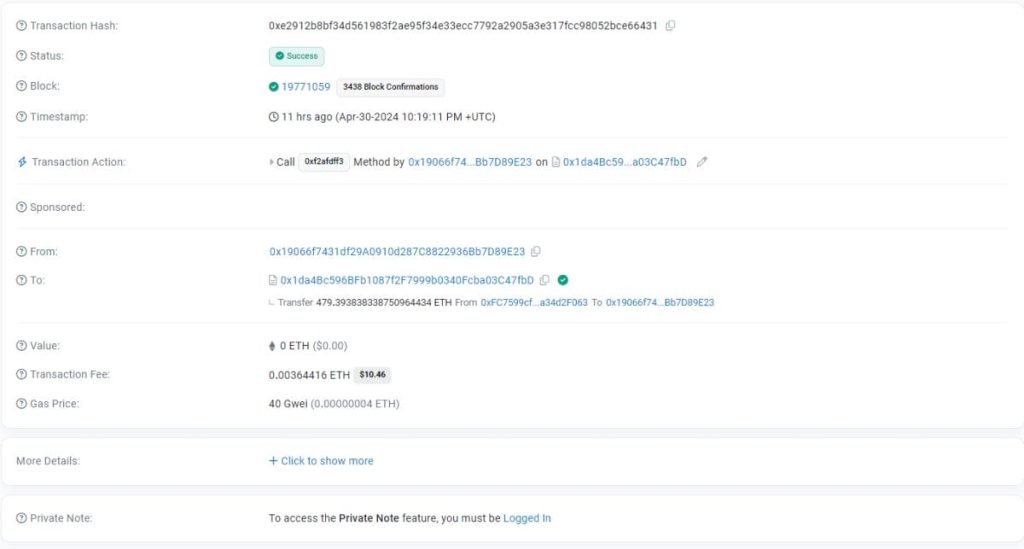
On April 30, Pike Finance fell victim to an exploit totaling $1.68 million across multiple blockchain networks, including Ethereum, Arbitrum, and Optimism. The incident was disclosed following a report issued by CertiK, an on-chain analytics firm.
According to CertiK’s findings, the attacker took advantage of a vulnerability within Pike Finance’s smart contract, allowing them to manipulate the output address. This exploit enabled the attacker to drain the contract of approximately $1.4 million in Ethereum, $150,000 in Optimism tokens, and $100,000 in Arbitrum tokens.
This exploit marks the second attack within a short timeframe, as Pike Finance previously experienced a $300,000 exploit on April 26.
Both attacks originated from a shared smart contract vulnerability, granting the attacker the ability to circumvent the contract’s controls. Pike addressed the issue via X to provide clarity on the matter.
Attention Users:
On the 30th of April 2024, the Pike Beta protocol was exploited for 99,970.48 ARB, 64,126 OP and 479.39 ETH.
This exploit is related to the initial USDC vulnerability that was reported last week on the 26th of April.
In order to pause the protocol, the spoke…
— Pike (@PikeFinance) May 1, 2024
In reaction to the incident, Pike has initiated an inquiry into the matter. They have announced a reward of 20%, totaling $336,000, for the restitution of the funds or any assistance in facilitating their recovery.
The crypto community has shifted its stance against Pike Finance.
Upon hearing the news, the community reacted with profound outrage. Pike users were left bewildered by the occurrence of the issue, especially considering that the exploit was permitted to occur once more following the initial attack. Despite facing significant criticism, Pike promptly responded by offering guidance to mitigate potential further losses and protect its users.
“Pike urges all users to revoke all approvals to prevent loss of funds. We recommend all users to review approvals immediately while we investigate.”
Amid escalating community backlash, Pike issued an update on their ongoing efforts to address the situation.
“Users can now claim refund for their pre-sale deposits, we had temporarily fixed the issue, but we are still investigating.”
Nevertheless, Pike’s current status remains uncertain as they advise users to “await further instructions” to be communicated via X.
Despite the issuance of refunds to users, attitudes toward Pike have undergone a notable shift. The delayed response to the initial attack paved the way for a subsequent one, jeopardizing the safety of its user base.
Users have begun to perceive Pike as an unreliable and unsafe platform, casting a shadow over its reputation.
The frequency of crypto hacks is decreasing.
Cryptocurrency hacks have experienced a significant reduction since 2021, with April recording the lowest monthly total loss of only $25.7 million.
The overall losses from exploits and scams decreased by 141% compared to the previous month, primarily due to a decrease in private key compromises. In March, there were 11 attacks on protocols resulting from private key compromises, whereas in April, this number reduced to only three.
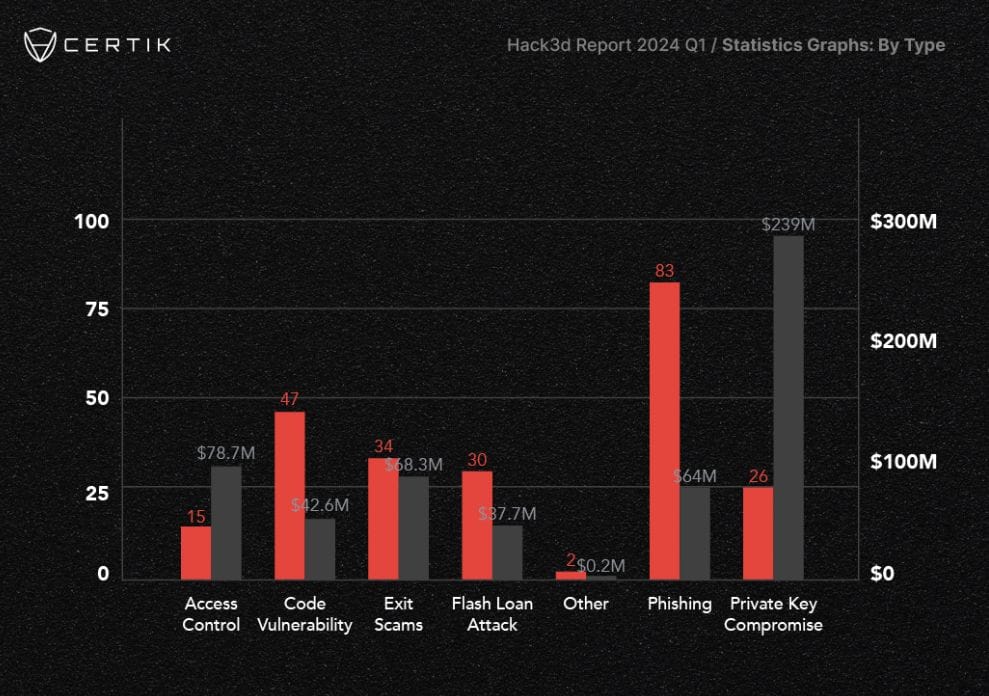
This demonstrates evident advancements in the cryptocurrency sphere, not just in terms of security enhancements but also in education. Individuals are becoming increasingly cognizant of safeguarding themselves against hacks and phishing attempts.
However, despite the notable reduction in incidents this month, crypto attacks persist as a substantial concern within the industry. CertiK reported that during the first quarter of 2024, over $502 million worth of digital assets were pilfered in 223 hacks and exploits.
This underscores the importance of vigilance and adherence to safe practices within the community, a point that Pike has emphasized, urging caution and prudent behavior among its members.
“Be on the lookout for scammers, impersonators and phishers during this volatile time. If you see posts mentioning a refund or airdrop – be sure to report the accounts responsible.”



